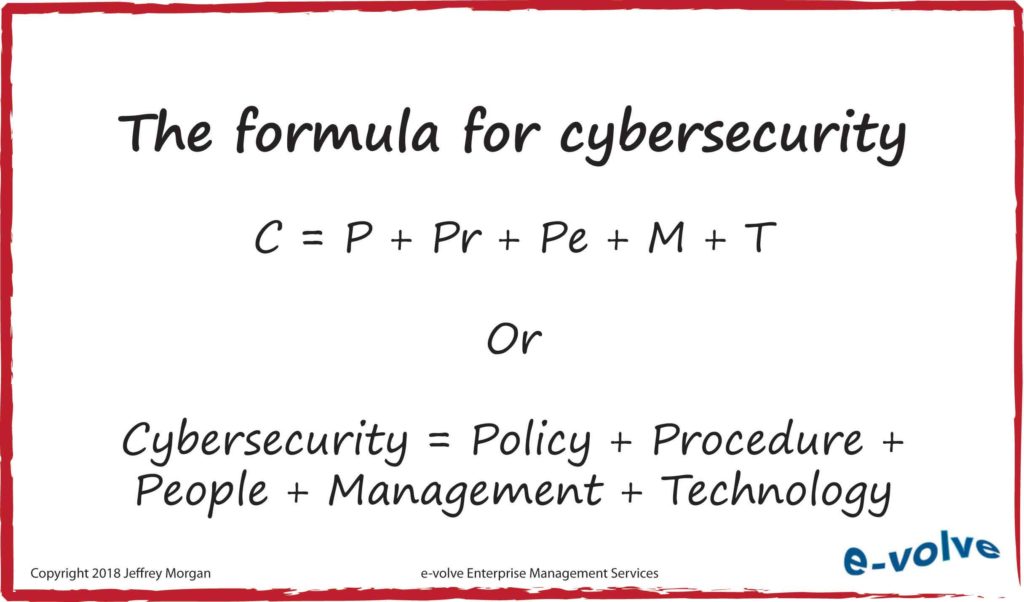
The Cybersecurity equation is so simple that I am always amazed at how often organizations get it wrong. Here it is:
Why do so many organizations get it wrong?
In many organizations, the equation is simply CYBERSECURITY = TECH. This is the wrong formula and it generally leads to disaster. I was talking to an executive in the financial industry the other day and I spouted my mantra, "Tech doesn't create great cybersecurity, policy and procedure do." Her response to me was, "A few years ago, I would have disagreed with you. Now, I am in agreement."
In complex organizations, which includes many or most organizations that fit the definition of a small business, the cyber and information risks can be huge. A small enterprise can have up to 500 employees and that definition includes 99.7 percent of firms in the United States. If you have more than a few employees working on computers or with information that might include PHI (Protected Health Information), PII (Personally Identifiable Information), or proprietary business information, you'd better have a cybersecurity plan that goes further than delegating information security responsibilities to an IT Director or Managed Service Provider.
This isn't meant to insult your IT staff or service providers. They do what they understand, but the information universe of an organization with hundreds or thousands of moving parts is typically too complex for them to fully comprehend and manage. If you look at the formula provided above you can see that there are at least five elements to a good cybersecurity program; IT providers can give you one of those elements. The other 80 percent of the equation is missing if you don't have a comprehensive plan that accounts for it all.
Policy
You must have a written security policy that comprehensively addresses all the information your organization manages and maintains, whether its paper, digital, or other. If you have a board of directors, the policy should be formally adopted by them. Likewise for county commissions and city councils.
A good way to develop policy is to establish a multidisciplinary committee of subject matter experts that represent a cross-section of the organization. Legal, HR, IT, corporate compliance, records management, executives, board members, and others should be represented on this committee. Developing your policy may take time - it could take a number of workgroups meetings and a few weeks to many months to write a comprehensive policy. The collective intelligence of the committee has a much higher IQ than any individuals in your organization.
Procedures
There must be written procedures for all the people who work with information. Your IT staff will have procedures for validating backups, monitoring logs, etc. Line-of-business managers and personnel may have procedures for managing departmental applications. When people perform procedures, they should be documented so there is an audit trail. This way, you'll know where to look if something goes wrong.
People
In information disasters, people are almost always the weak link. They make mistakes, they forget to do things. 90 percent of all cybersecurity problems are caused by people, so why do most organization focus almost all their cybersecurity resources on technology? It's lazy management. People need training, supervision, and encouragement. Sometimes people need disciplinary action.
Management
By management, I mean the head honchos, big kahunas, top dogs, and big enchiladas. I am talking about El Jefe. Last year, the acting CEO of Equifax testified before a congressional committee that he didn't know whether or not his company was encrypting consumer data. How humiliating! Do you want to be in that position? Information security is a core management responsibility. This doesn't mean that you, the executive need to understand minute technical details of specific security controls, but it does mean you have to know what's going on in your enterprise. In every major framework for information and cybersecurity, management participation is a requirement.
According to Deming, 94 percent of all problems in an organization are due to management failures. While I am sure that his assessment is statistically correct, it's been my professional experience that closer to 100 percent of problems are due to poor management and cybersecurity is no exception.
Management of your cybersecurity program will flow in all directions from the top down to the bottom up. It is a good idea to have a board committee dedicated to cybersecurity.
Technology
The basic business rule is to only apply technology once you understand all your processes. Business enterprises get this wrong all the time. There is always a rush to implement technology as if it is a solution. Technology is not a solution; it's a tool. If you don't understand all your processes and procedures, you'll choose the wrong tool.
Different organizations with different security postures and risk appetites will need different technology.
Technology will definitely be part of your cybersecurity program, but it shouldn't be the whole program.
Resources
Resources for building cybersecurity programs are free or cheap so there's no excuse for procrastination. A couple of resources for developing comprehensive programs include:
The Framework for Improving Critical Infrastructure Cybersecurity
The NIST Cybersecurity Framework is free from the US Government and takes a risk-based approach to cybersecurity.
ISO/IEC 27001
This is the international standard for information security management systems and it is $138 from the ANSI Web Store.
Need Help?
If you want help building your program, contact us and let's talk.
Copyright 2018, Jeffrey Morgan